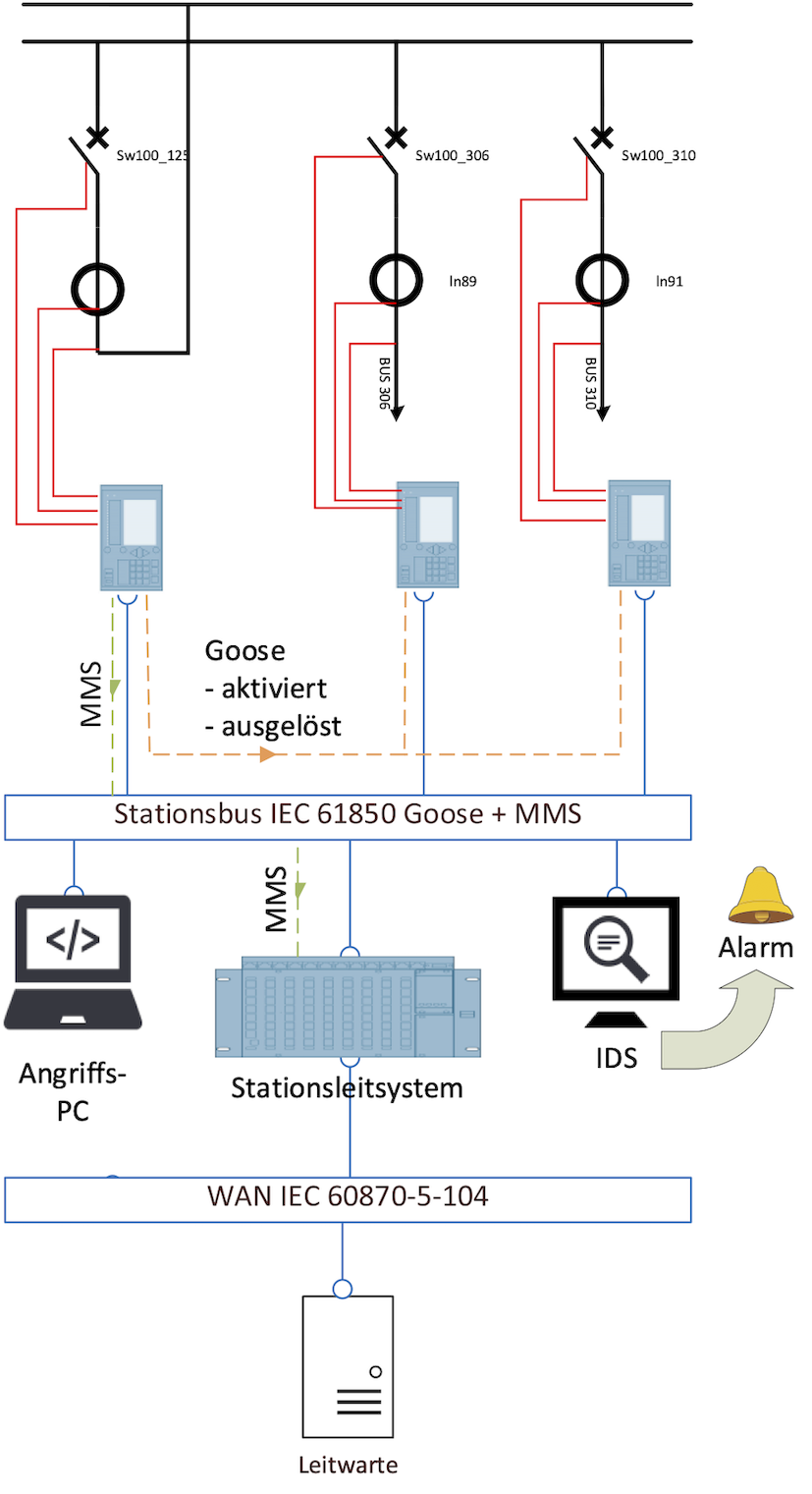
To enhance ICT security in InnoSys 2030, the concepts developed will be analyzed for potential weaknesses and new types of threats to reliable and secure system operation. The findings obtained in the threat analysis will form the basis for secure implementation of the concepts. These preventative measures will also be supplemented by the development and evaluation of detection methods for cyber attacks within the ICT network, where integrating contextual knowledge has been shown to be particularly promising in terms of enabling a rapid, targeted response in the event of unavoidable security incidents in the future.
ICT security requirements and specifications were defined as the basis for evaluating ICT security, particularly those from a white paper published by the German Association of Energy and Water Industries (Bundesverband der Energie- und Wasserwirtschaft e.V. (BDEW)). While many such criteria focus on implementation details or contractual agreements during the implementation phase, the focus of InnoSys 2030 is on design support via security-by-design to enable secure implementation of the measures and concepts developed.
Thus, ICT security was evaluated with special attention to those evaluation criteria that can be recorded as early as the design level, but at the same time are highly relevant to real-world implementation of ICT security. Concept descriptions, responses to a specially developed questionnaire, and discussions with those responsible for the concepts were used to assess the ICT security of the measures and concepts. With this as a basis, the evaluation of the measures and concepts with regard to ICT security was validated with those responsible for the concept and then reviewed later in the project on the basis of findings from demonstrators and field tests and, if necessary, adapted to the new insights.
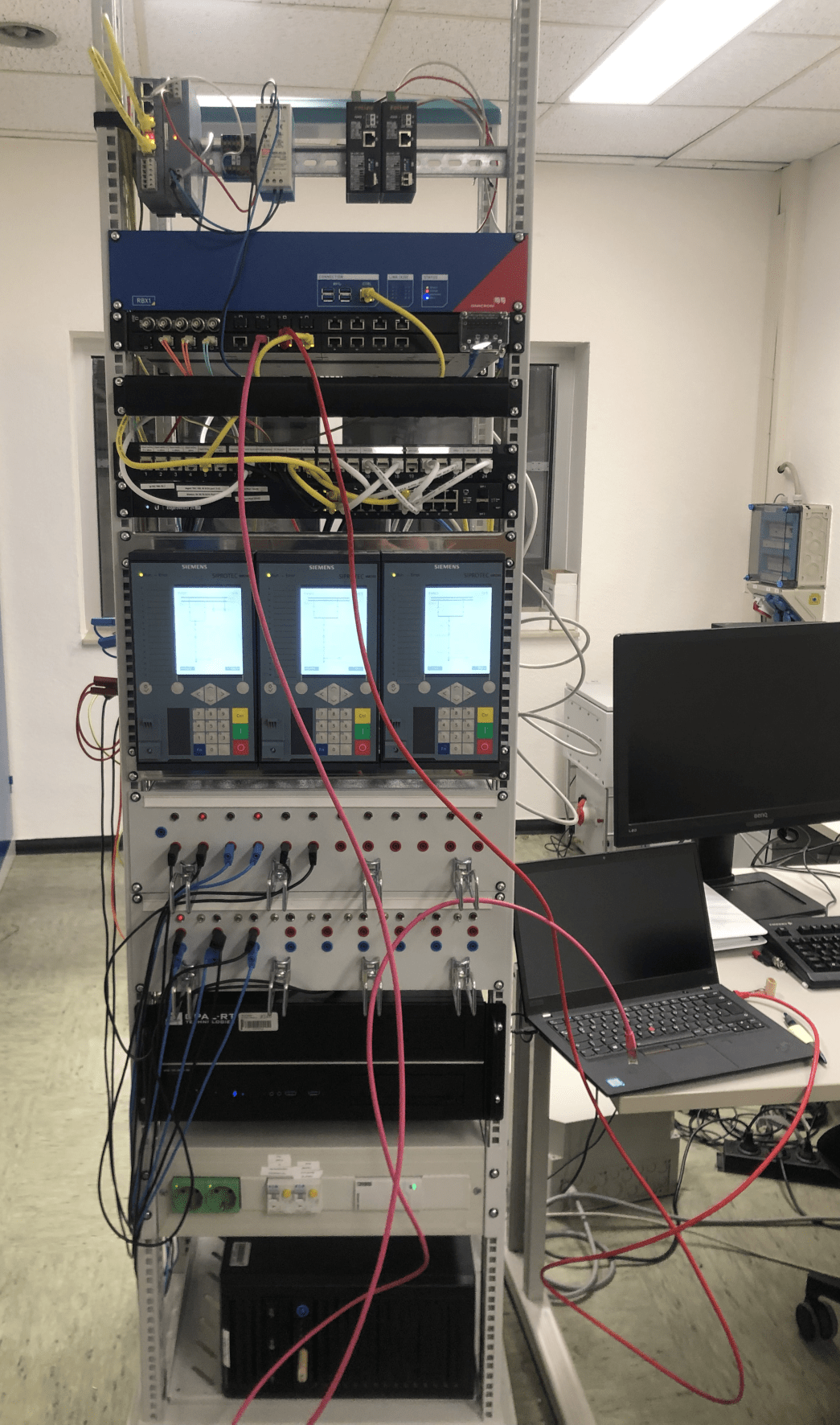
In addition to these preventive security measures, InnoSys 2030 also looked more closely at methods for detecting cyber attacks to enable a rapid, targeted response to new threats. Different types of attacks were then simulated in a practical test setup to evaluate and compare the performance of various detection methods. This included both the relevant published detection methods and proprietary methods developed in-house.